Sign up to the newsletter
Sign up to the Digital Security by Design newsletter to stay up to date with our events, news, insights and opportunities. Be the first to know about our work and ways to get involved.
The CHERI (Capability Hardware Enhanced RISC Instructions) architecture extensions designed by the University of Cambridge and SRI International extends the CPU instruction set to enable it to access memory using capabilities instead of machine-word pointers. Capabilities provide fine-grained hardware-enforced access protection of objects in memory. A program using capabilities is generally incapable of making out-of-bounds accesses, which means bugs can be caught and fixed instead of exploited. Applied to existing languages that lack memory safety, like C and C++, this technology has the potential to address memory safety issues without the overhead of software runtime checks.
A key benefit of the CHERI technology is that it can be applied to legacy C or C++ programs with minimal changes – you don’t need to rewrite all of your software in a new language. Watch this video to learn more about CHERI and safe languages.
CHERI also provides the ability to create distinct compartments within one process which can be used to harden a system against attack. Compartments are a high-performance mechanism to subdivide an application into portions that can interact in a very controlled way. Sensitive subsystems can be segregated from the rest of an application, reducing the potential for exploitation.
Morello is a research programme led by Arm which focuses on new ways to make processors more robust in future, and be able to deter some types of security breaches.
Arm designed a prototype architecture using the CHERI concepts, and has now developed prototype silicon with this new technology. This prototype System on Chip (SoC) is the heart of the Morello development board.
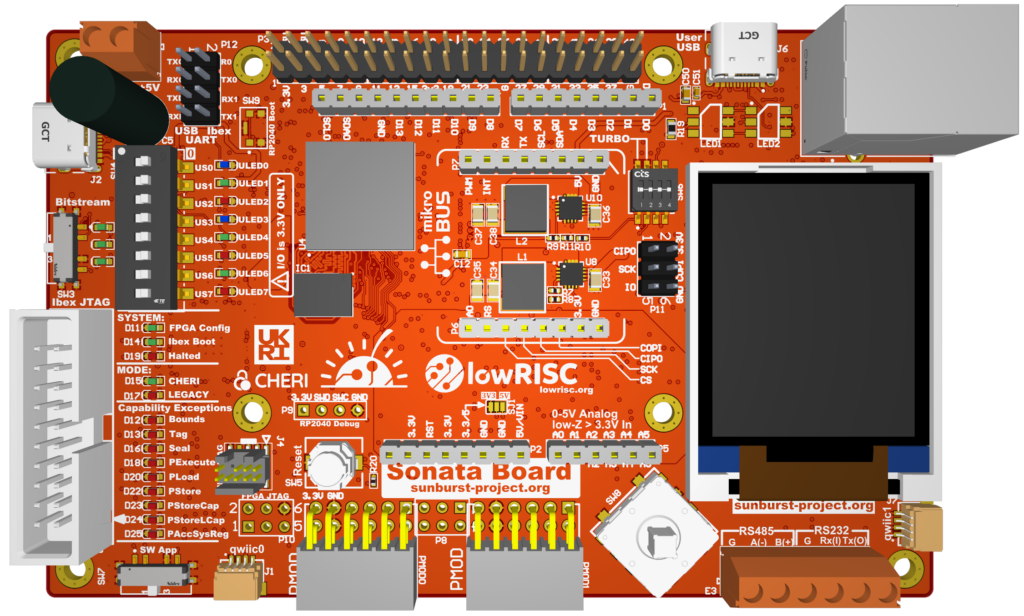
A low cost development board for investigating CHERI security enhancements. Sonata is a system for evaluating the usage of CHERIoT Ibex core as a microcontroller for embedded, IoT and Operational Technology applications. The system contains a number of peripherals (I2C, SPI, GPIO, USB, and UART) and the CHERIoT Ibex core itself.
It is designed for use on FPGA and specifically targets the Sonata FPGA board, but as the entire design (from example PCB to software) is open-source it can be run on any similar system.

The documents and code repositories needed to get started with the CHERI architecture and work with the Morello prototype architecture and board.
Sign up to the Digital Security by Design newsletter to stay up to date with our events, news, insights and opportunities. Be the first to know about our work and ways to get involved.